Imports System.Diagnostics
Public Class Form1
Private TargetProcessHandle As Integer
Private pfnStartAddr As Integer
Private pszLibFileRemote As String
Private TargetBufferSize As Integer
Dim proc As Process
Public Const PROCESS_VM_READ = &H10
Public Const TH32CS_SNAPPROCESS = &H2
Public Const MEM_COMMIT = 4096
Public Const PAGE_READWRITE = 4
Public Const PROCESS_CREATE_THREAD = (&H2)
Public Const PROCESS_VM_OPERATION = (&H8)
Public Const PROCESS_VM_WRITE = (&H20)
Dim DLLFileName As String
Public Declare Function ReadProcessMemory Lib "kernel32" (
ByVal hProcess As Integer,
ByVal lpBaseAddress As Integer,
ByVal lpBuffer As String,
ByVal nSize As Integer,
ByRef lpNumberOfBytesWritten As Integer) As Integer
Public Declare Function LoadLibrary Lib "kernel32" Alias "LoadLibraryA" (
ByVal lpLibFileName As String) As Integer
Public Declare Function VirtualAllocEx Lib "kernel32" (
ByVal hProcess As Integer,
ByVal lpAddress As Integer,
ByVal dwSize As Integer,
ByVal flAllocationType As Integer,
ByVal flProtect As Integer) As Integer
Public Declare Function WriteProcessMemory Lib "kernel32" (
ByVal hProcess As Integer,
ByVal lpBaseAddress As Integer,
ByVal lpBuffer As String,
ByVal nSize As Integer,
ByRef lpNumberOfBytesWritten As Integer) As Integer
Public Declare Function GetProcAddress Lib "kernel32" (
ByVal hModule As Integer, ByVal lpProcName As String) As Integer
Private Declare Function GetModuleHandle Lib "Kernel32" Alias "GetModuleHandleA" (
ByVal lpModuleName As String) As Integer
Public Declare Function CreateRemoteThread Lib "kernel32" (
ByVal hProcess As Integer,
ByVal lpThreadAttributes As Integer,
ByVal dwStackSize As Integer,
ByVal lpStartAddress As Integer,
ByVal lpParameter As Integer,
ByVal dwCreationFlags As Integer,
ByRef lpThreadId As Integer) As Integer
Public Declare Function OpenProcess Lib "kernel32" (
ByVal dwDesiredAccess As Integer,
ByVal bInheritHandle As Integer,
ByVal dwProcessId As Integer) As Integer
Private Declare Function FindWindow Lib "user32" Alias "FindWindowA" (
ByVal lpClassName As String,
ByVal lpWindowName As String) As Integer
Private Declare Function CloseHandle Lib "kernel32" Alias "CloseHandleA" (
ByVal hObject As Integer) As Integer
Dim ExeName As String = IO.Path.GetFileNameWithoutExtension(Application.ExecutablePath)
Private Sub Inject()
On Error GoTo 1
Timer1.Stop()
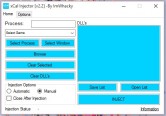
Dim TargetProcess As Process() = Process.GetProcessesByName(TextBox1.Text)
TargetProcessHandle = OpenProcess(PROCESS_CREATE_THREAD Or PROCESS_VM_OPERATION Or PROCESS_VM_WRITE, False, TargetProcess(0).Id)
pszLibFileRemote = OpenFileDialog1.FileName
pfnStartAddr = GetProcAddress(GetModuleHandle("Kernel32"), "LoadLibraryA")
TargetBufferSize = 1 + Len(pszLibFileRemote)
Dim Rtn As Integer
Dim LoadLibParamAdr As Integer
LoadLibParamAdr = VirtualAllocEx(TargetProcessHandle, 0, TargetBufferSize, MEM_COMMIT, PAGE_READWRITE)
Rtn = WriteProcessMemory(TargetProcessHandle, LoadLibParamAdr, pszLibFileRemote, TargetBufferSize, 0)
CreateRemoteThread(TargetProcessHandle, 0, 0, pfnStartAddr, LoadLibParamAdr, 0, 0)
CloseHandle(TargetProcessHandle)
1: Me.Show()
End Sub
Private Sub Button1_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button1.Click
TextBox1.Clear()
End Sub
Private Sub Button2_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button2.Click
If IO.File.Exists(OpenFileDialog1.FileName) Then
End If
Dim TargetProcess As Process() = Process.GetProcessesByName(TextBox1.Text)
If TargetProcess.Length = 0 Then
Label3.Text = ("Waiting for: " + TextBox1.Text + ".exe...")
Else
Timer1.Stop()
Label3.ForeColor = Color.Green
Label3.Text = "Injection Successful!"
Call Inject()
If CheckBox1.Checked = True Then
Me.Close()
Else
End If
End If
End Sub
Private Sub Button3_Click(ByVal sender As System.Object, ByVal e As System.EventArgs)
Close()
End Sub
Private Sub Button4_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button4.Click
OpenFileDialog1.Filter = "DLL|*.dll"
OpenFileDialog1.ShowDialog()
Dim FileName As String
FileName = OpenFileDialog1.FileName.Substring(OpenFileDialog1.FileName.LastIndexOf("\"))
Dim DllFileName As String = FileName.Replace("\", "")
Me.Dlls.Items.Add(DllFileName)
End Sub
Private Sub Button5_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button5.Click
For i As Integer = (Dlls.SelectedItems.Count - 1) To 0 Step -1
Dlls.Items.Remove(Dlls.SelectedItems(i))
Next
End Sub
Private Sub Button6_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button6.Click
Dlls.Items.Clear()
End Sub
Private Sub Timer1_Tick(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Timer1.Tick
If IO.File.Exists(OpenFileDialog1.FileName) Then
Dim TargetProcess As Process() = Process.GetProcessesByName(TextBox1.Text)
If TargetProcess.Length = 0 Then
Label3.Text = ("Waiting for:" + TextBox1.Text + ".exe" + "....")
Else
Timer1.Stop()
Label3.Text = "Injection Successful!"
Call Inject()
If CheckBox1.Checked = True Then
Me.Close()
End If
End If
End If
End Sub
Private Sub Form1_Load(ByVal sender As System.Object, ByVal e As System.EventArgs)
Timer1.Interval = 2
Timer1.Start()
Label6.Visible = False
ProgressBar1.ForeColor = Color.Cyan
End Sub
Private Sub RadioButton1_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles RadioButton1.CheckedChanged
Timer1.Start()
End Sub
Private Sub RadioButton2_CheckedChanged(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles RadioButton2.CheckedChanged
Timer1.Stop()
End Sub
Private Sub Form1_Load_1(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load
ShowIcon = True
End Sub
Private Sub Button7_Click_1(sender As Object, e As EventArgs) Handles Button7.Click
For Each proc As Process In Process.GetProcesses
ListBox1.Items.Add(proc.ProcessName)
Next
ProgressBar1.Value = 100
Label7.Text = ProgressBar1.Value
Label6.Visible = True
End Sub
Private Sub Button8_Click(sender As Object, e As EventArgs) Handles Button8.Click
TextBox1.Text = ListBox1.SelectedItem
End Sub
Private Sub ListBox1_SelectedIndexChanged(sender As Object, e As EventArgs) Handles ListBox1.SelectedIndexChanged
TextBox1.Text = ListBox1.SelectedItem
End Sub
Private Sub Label2_Click(sender As Object, e As EventArgs) Handles Label2.Click
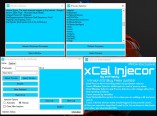
MessageBox.Show("Made by ImWhacky (eblank)" & vbCrLf & "If you have any errors, report them to the [censored] thread and i will try to fix them in the next update." & vbCrLf & " " & vbCrLf & "Thanks!",
"xCal v1.5")
End Sub
End Class