
|
|
|
dretlock
|
danke fur die program |

|
|
|
olaf1234
|
can i remove the hacks from the exe ? |

|
|
|
dretlock
|
danke |

|
|
|
olaf1234
|
can i uninject it ? ( some tools ) |

|
|
|
System
|
Kategorie: Tools Entwickler: DarthTon Beschreibung: - Supports x86 and x64 processes and modules - Kernel-mode injection feature (driver required) - Manual map of kernel drivers (driver required) - Injection of pure managed images without proxy dll - Windows 7 cross-session and cross-desktop injection - Injection into native processes (those having only ntdll loaded) - Calling custom initialization routine after injection - Unlinking module after injection - Injection using thread hijacking - Injection of x64 images into WOW64 process - Image manual mapping - Injection profiles Manual map features: - Relocations, import, delayed import, bound import - Static TLS and TLS callbacks - Security cookie - Image manifests and SxS - Make module visible to GetModuleHandle, GetProcAddress, etc. - Support for exceptions in private memory under DEP - C++/CLI images are supported (use 'Add loader reference' in this case) Kernel manual map features are mostly identical to user-mode with few exceptions: - No C++ exception handling support for x64 images (only SEH) - No static TLS - No native loader compatibility - Limited dependency path resolving. Only API set schema, SxS, target executable directory and system directory Supported OS: Win7 - Win10 x64 Changelog: +V2.3.0 - Win10 Creators Update support - Unified injection and manual mapping (injector -> target) : x86->x86, x64->x64, x86->x64, x64->x86 - Bug fixes, stability improvements Screenshots: 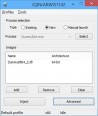 Download: Xenos 2.3.0 |

|
|
|
MENEMJO
|
Kategorie: Tools Entwickler: DarthTon Beschreibung: Features: - Supports x86 and x64 processes and modules - Injection of pure managed images without proxy dll(code was partially stolen from _Mike@OC) - Windows 7 cross-session and cross-desktop injection - Injection into native processes (those that only have ntdll loaded) - Calling custom initialization routine after injection - Unlinking module after injection - Injection using thread hijacking - Injection of x64 images into WOW64 process(read more in Additional notes section) - Image manual mapping Changelog V1.0.1: - Fixed bug with remote memory deallocation after manual mapping - Exception handler aren't created now if process has DEP turned off. Supported OS - Win7 - Win8.1 x64. Should also work on x86 OS versions but I haven't tested it much. Screenshots: 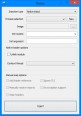 Download: Xenos Injector 1.0.1 |

|
|
|
otocu
|
Thank you for your support. I like it. |

|
|
|
KN4CK3R
|
Kategorie: Tools Entwickler: DarthTon Beschreibung: - Supports x86 and x64 processes and modules - Kernel-mode injection feature (driver required) - Manual map of kernel drivers (driver required) - Injection of pure managed images without proxy dll - Windows 7 cross-session and cross-desktop injection - Injection into native processes (those having only ntdll loaded) - Calling custom initialization routine after injection - Unlinking module after injection - Injection using thread hijacking - Injection of x64 images into WOW64 process - Image manual mapping - Injection profiles Manual map features: - Relocations, import, delayed import, bound import - Static TLS and TLS callbacks - Security cookie - Image manifests and SxS - Make module visible to GetModuleHandle, GetProcAddress, etc. - Support for exceptions in private memory under DEP - C++/CLI images are supported (use 'Add loader reference' in this case) Kernel manual map features are mostly identical to user-mode with few exceptions: - No C++ exception handling support for x64 images (only SEH) - No static TLS - No native loader compatibility - Limited dependency path resolving. Only API set schema, SxS, target executable directory and system directory Supported OS: Win7 - Win10 tech preview x64 Changelog +V2.1.1 - Added some logging Screenshots:  Download: Xenos 2.1.1 |

|
|
|
KN4CK3R
|
Kategorie: Tools Entwickler: DarthTon Beschreibung: - Supports x86 and x64 processes and modules - Kernel-mode injection feature (driver required) - Manual map of kernel drivers (driver required) - Injection of pure managed images without proxy dll - Windows 7 cross-session and cross-desktop injection - Injection into native processes (those having only ntdll loaded) - Calling custom initialization routine after injection - Unlinking module after injection - Injection using thread hijacking - Injection of x64 images into WOW64 process - Image manual mapping - Injection profiles Manual map features: - Relocations, import, delayed import, bound import - Static TLS and TLS callbacks - Security cookie - Image manifests and SxS - Make module visible to GetModuleHandle, GetProcAddress, etc. - Support for exceptions in private memory under DEP - C++/CLI images are supported (use 'Add loader reference' in this case) Supported OS: Win7 - Win10 tech preview x64 Changelog + V2.0.0 - New GUI - Injection image list - Auto-injection - Injection profiles - Injection delay timers - Kernel injection improvements - module unlinking and init routine invocation - Win10 tech preview support Screenshots:  Download: Xenos 2.0.0 |

|
|
|
KN4CK3R
|
Kategorie: Tools Entwickler: DarthTon Beschreibung: Features: - Supports x86 and x64 processes and modules - Kernel injection (no process handle required) - Injection of pure managed images without proxy dll(code was partially stolen from _Mike@OC) - Windows 7 cross-session and cross-desktop injection - Injection into native processes (those that only have ntdll loaded) - Calling custom initialization routine after injection - Unlinking module after injection - Injection using thread hijacking - Injection of x64 images into WOW64 process(read more in Additional notes section) - Image manual mapping Changelog + V1.2.0 - Kernel injection methods - Various bug fixes V1.1.2 - Save/load last programm configuration - Added command line for process launcher - ManualMap: Discardable sections aren't mapped now (e.g. ".reloc") V1.1.0 - Added module view - Module unloading V1.0.1: - Fixed bug with remote memory deallocation after manual mapping - Exception handler aren't created now if process has DEP turned off. Supported OS - Win7 - Win8.1 x64. Should also work on x86 OS versions but I haven't tested it much. Screenshots:  Download: Xenos 1.2.0 |